New Mac Malware Uses ‘Fileless’ Technique To Attack Stealthily

Notorious hacking group Lazarus which is also behind the widespread WannaCry ransomware is trying to infect Mac users with new malware that uses ‘fileless’ technique to hide from antivirus software.
As highlighted by Patrick Wardle, a Mac security expert, this new malware deploys in-memory execution or fileless infection that involves malware not writing anything to your device’s hard drive. The malicious code is loaded directly into memory and executed from there. This technique makes it difficult for endpoint detection software to spot it as there is no file to be flagged.
However, there is a silver lining — the malware isn’t completely fileless as the first stage involves installing a cryptocurrency app dubbed UnionCryptoTrader.dmg. According to VirusTotal, now 17 out of 57 malware detection software can spot it. Previously, this number was just 2 when the malware was brought to light earlier this week.
Patrick Wardle’s analysis details the working of the malware and it can perform the following operations:
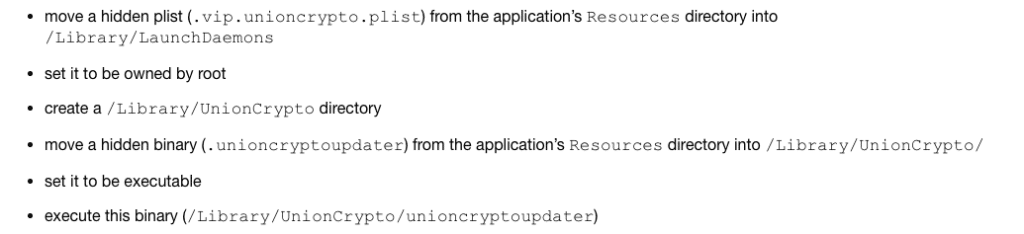
This results in a binary named unioncryptoupdated that runs as root and can also survive a reboot.
The reason why researchers think that Lazarus is behind this malware is the fact that the plist and binary of the launch daemon are stored in the resource directory of the application. This is a technique particularly used by the Lazarus group.
In his blog, Patrick Wardle writes: “As the layout of an in-memory process image is different from its on disk-in image, one cannot simply copy a file into memory and directly execute it. Instead, one must invoke APIs such as NSCreateObjectFileImageFromMemory and NSLinkModule (which take care of preparing the in-memory mapping and linking).”
The malware usually targets those who are involved in cryptocurrency trading. To steer clear of the malware and protect yourself, ensure that you do not install any suspicious app from the internet.
Also Read: SyncStop Is A USB Condom That You Need To Protect Your Data