Here’s What A Phishing Attack On Instagram Looks Like Today

Researchers at Sophos have discovered an uncommon phishing campaign targeted at Instagram users.
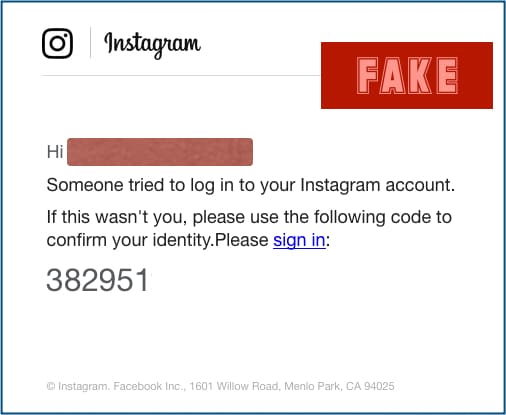
The new attack includes receiving an authentic-looking two-factor authorization email. After clicking on the sign-in link, the user is taken to a fake Instagram login page, which is a pretty standard way to steal login conditionals.
Starting from the email to the two-factor authentication (2FA) code and the Instagram login page, every single aspect of it is fake. However, the issue at large is the realness of it all. Even the Sophos researchers said that the attack is much more believable than the other standard phishing attacks.
“We don’t like to admit it, but the crooks thought this one through.” the researchers said. The interesting part is the usage of a two-factor authorization code, “a nice touch” from their end. While there were a few punctuation errors in the email, the team admitted the message to be “clean, clear and low-key enough not to raise instant alarm bells.”
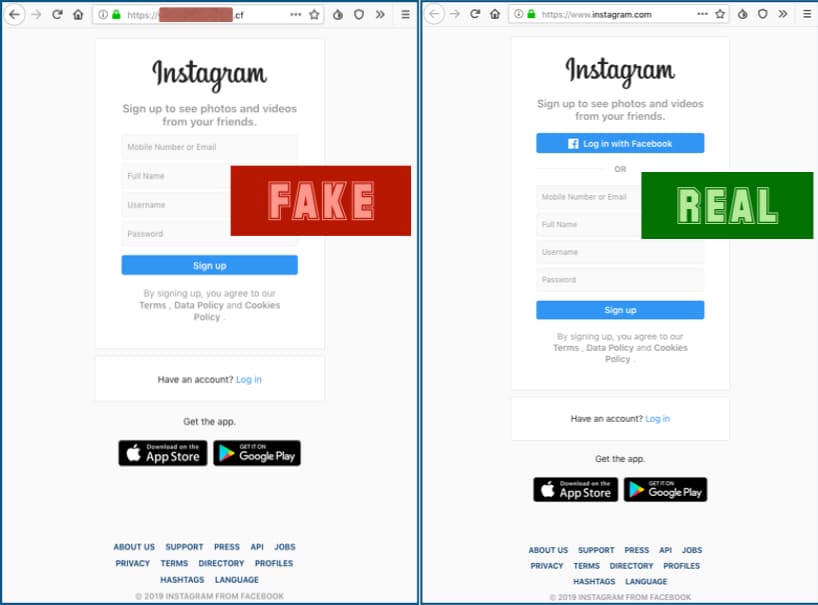
Same goes with the fake Instagram login page — hackers registered the webpage under a ‘.cf’ (Centrafrique) domain. Researchers believe the crooks didn’t go way too far with it and bought a free domain “that nearly spells login, but doesn’t quite.”
However, the most frightening part of the phishing page was the HTTPS padlock near the URL. Many people stop worrying about security as soon as they see that green icon.
A valid HTTPS certificate means that the connection to a website is secure, but it doesn’t claim responsibility for the underlying content on the webpage. Nonetheless, an HTTP padlock with a touch of two-factor authentication does make it the perfect recipe to dupe Instagram users.
Researchers advise users to always be receptive for the red flags while giving login credentials. The team also ask users to avoid signing-in through suspicious authorization emails instead manually go to the concerned website through the web browser or app. In the end, it depends on how much vigilant you are while using the internet.
Also Read: Two Researchers Recreate The “Dangerous” OpenAI Text Generator