WhatsApp Vulnerability Lets Attackers Alter Your Messages And Spread Fake News
A new vulnerability has surfaced in WhatsApp’s encryption method that allows attackers to alter messages and…

A new vulnerability has surfaced in WhatsApp’s encryption method that allows attackers to alter messages and…

By this time, we have realized how artificial intelligence is a boon and a bane at…
Many of us already know that the internet traffic passes through different countries before reaching its…
It seems that efforts being made by Google and Mozilla to safeguard their Chrome and Firefox…
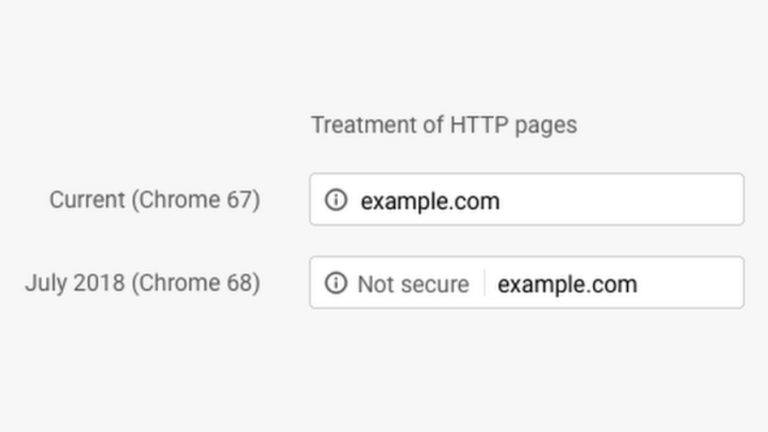
Google is taking the privacy quite seriously, and the new Chrome security update will undoubtedly put…

In the past, the security researchers have come across cases where notorious hackers were able to…
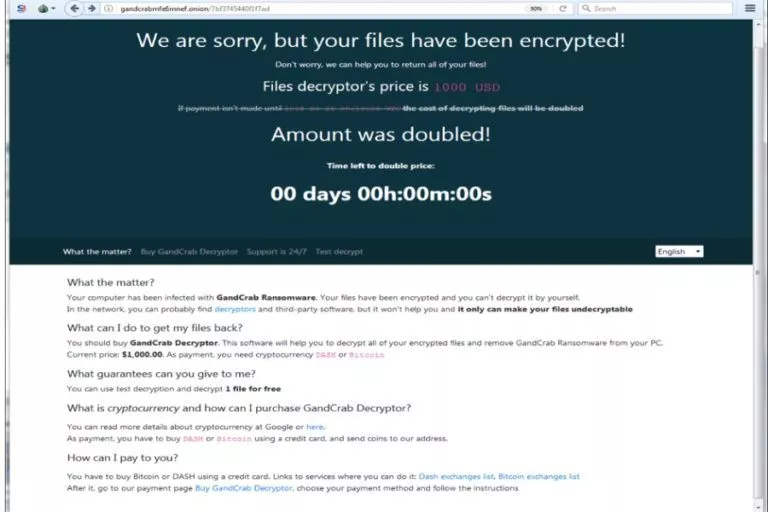
GandCrab ransomware, which has created a hullabaloo in the cybersecurity industry by constantly evolving, has yet…
After receiving complaints regarding abnormal battery discharge across different models of iPhone, Apple has released iOS…

Amazon is selling its facial recognition technology called Rekognition to the American law enforcement agencies — this…

Rakhni Trojan which was first discovered in 2013 has evolved over the course of five years….