Google Slammed For Giving Gmail Access To Third Party Developers (Humans)
There are many third-party apps that require access to your Gmail account. For instance, the ones…
There are many third-party apps that require access to your Gmail account. For instance, the ones…

On May 23rd, The American intelligence agency NSA started the process of deleting the call records it has…
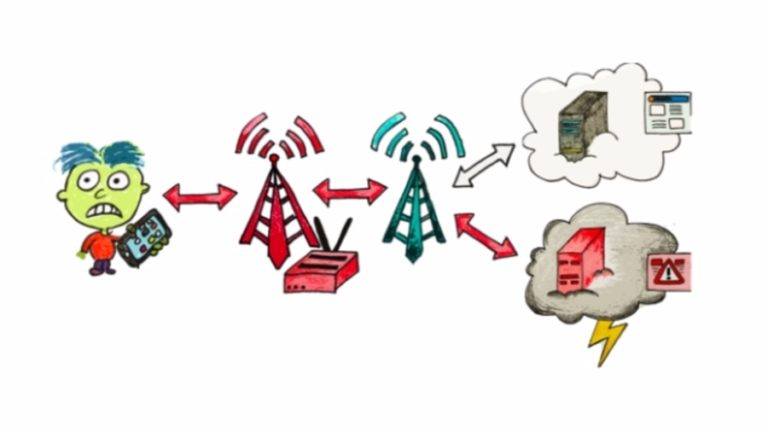
The Long Term Evolution (LTE) standard for mobile communication, also known as 4G was designed to overcome…
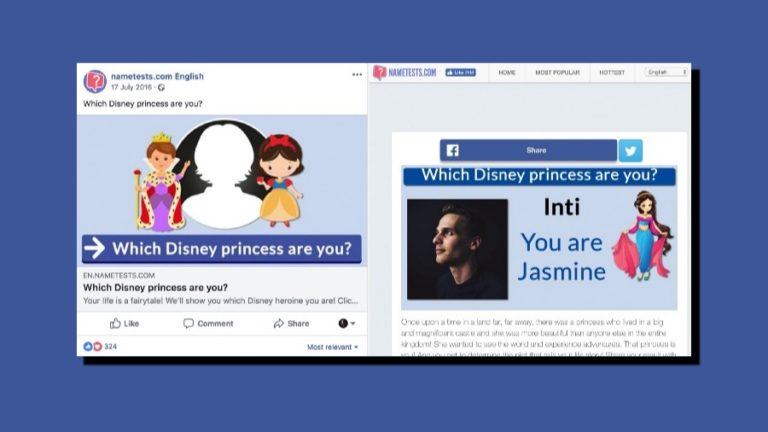
When Facebook-Cambridge Analytica scandal started blazing up headlines, many Facebook critics and security experts called it…

A new research has proved that the battery in your cell phone could be turned into a…

In addition to making you anonymous, the Tor network also gives access to the world of…

Over the past years, Apple has been playing cat and mouse with the security researchers and…

A new malware that targets banking apps has hit Android devices. Names MysteryBot, the malware packs…

It seems that the cat and mouse chase between Apple and people who want to get…

Security researchers have found a critical flaw in Windows 10 where Cortana can be manipulated into…