Using BitTorrent For Downloading? This Security Flaw Lets Hackers Control Your PC Remotely
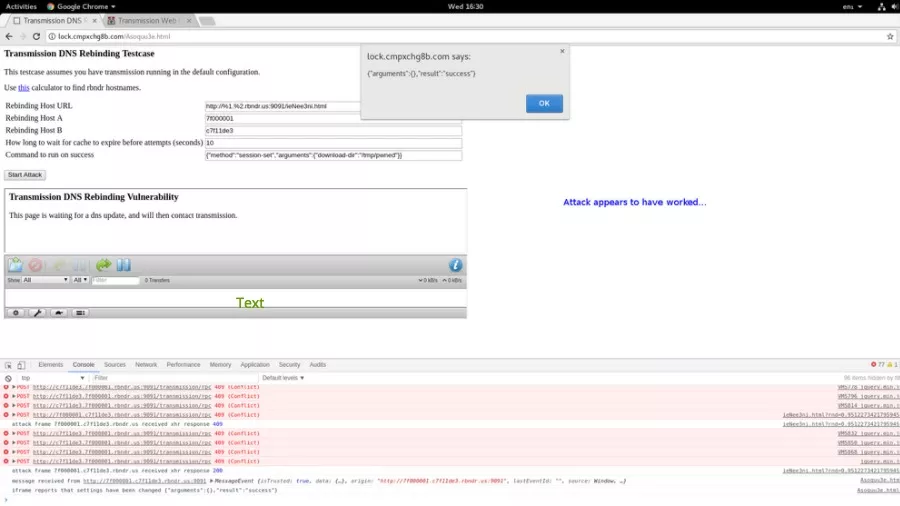
A recent critical vulnerability spotted by Google’s Project Zero team targets the popular Transmission BitTorrent app. By exploiting this flaw, a hacker can execute malicious code on the users’ computer, according to Ars Technica.
Last week, the Project Zero researchers published the proof-of-concept attack code. It’s worth noting that Project Zero normally refrains itself from making the details of such flaws public for 90 days or until the fix is released. However, in this case, the flaw was made public only 40 days after the initial report. This happened because the report included a patch to fix the vulnerability but Transmission developers didn’t respond on their private security mailing list.
After the public release of the flaw, the downstream projects using the Transmission project would be able to inculcate the patch in their implementations.
First of a few remote code execution flaws in various popular torrent clients, here is a DNS rebinding vulnerability Transmission, resulting in arbitrary remote code execution. https://t.co/kAv9eWfXlG
— Tavis Ormandy (@taviso) January 11, 2018
With the help of a hacking technique called domain name system rebinding, this exploit can control the Transmission interface when the target visits a malicious website. This can be further made easier by creating a DNS name which attacker is authorized to communicate with.
After controlling the Transmission interface, the attacker needs to change the torrent download directory to home and download a torrent named .bashrc. The attacker can also configure Transmission to run any command after the download has completed.
The Transmission developers have promised to release the fix as soon as possible. However, no specific date was given.
Also Read: Beware! Fake Spectre & Meltdown Patches Are Infecting PCs With “Smoke Loader” Malware






