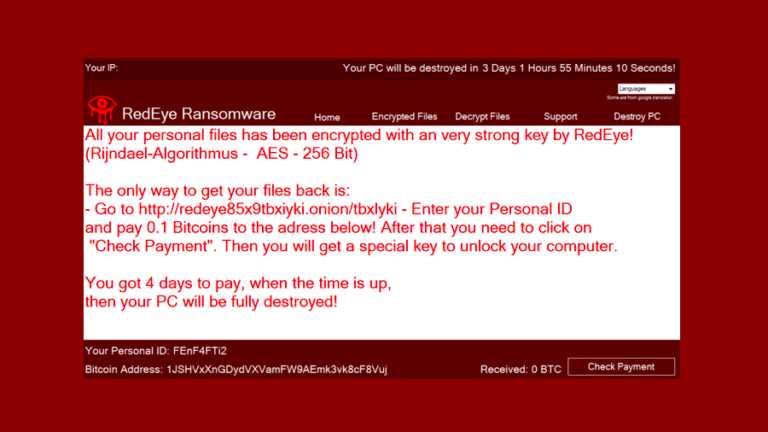
RedEye Ransomware Destroys Your PC Files If Payment Isn’t Made
Cyptojacking is the latest buzzword in the cybersecurity world. The notorious cybercriminals have taken the advantage…
Cyptojacking is the latest buzzword in the cybersecurity world. The notorious cybercriminals have taken the advantage…
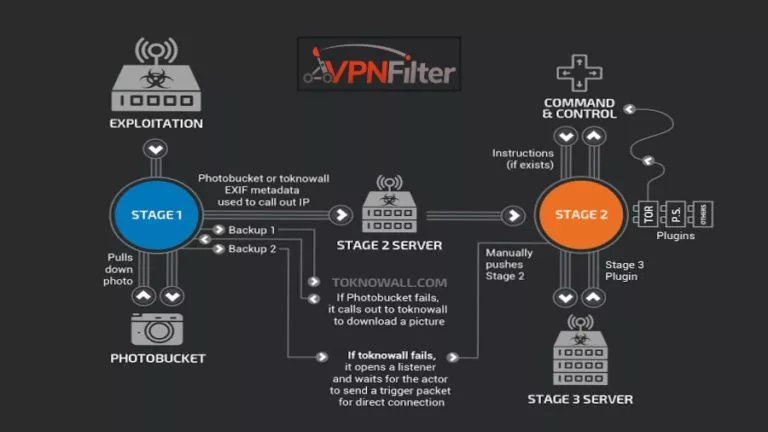
In late May, Cisco security researchers uncovered a router-hacking malware named VPNFilter, which was reported to…

Do you own a OnePlus 6 or planning to buy one? If yes, you might want…

You might have heard the word Social Engineering. But, what exactly is Social Engineering? What are…

Very often a significant security flaw is followed by new derivatives of the same exploit. Following…

The word Cambridge now reminds most of us about Cambridge Analytica and Alexandr Kogan. A report…

Email users who use PGP (based on OpenPGP) and S/MIME to encrypt and decrypt their communications…

Tarwirdur, a Github user, recently flagged a malicious cryptocurrency mining malware hiding in Ubuntu apps. Found…

We might have a hint, but we never let our brain trick us into the fact…
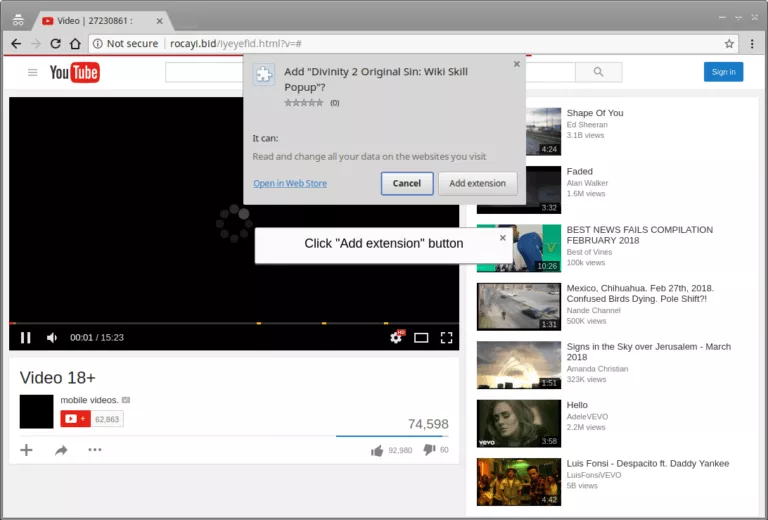
We have seen many examples where malicious chrome extensions are used to target users and steal…