Which Phones Will Get Android 7.0 Nougat Update — The Complete List
Short Bytes: As the Android 7.0 Nougat is here, people are searching the web to know…
How to articles revolve around simple and useful tips to improve productivity of your computers, phones and other devices. We have a section for art and literature lovers too. Our other features include news from health, education, environment and society.

Short Bytes: As the Android 7.0 Nougat is here, people are searching the web to know…
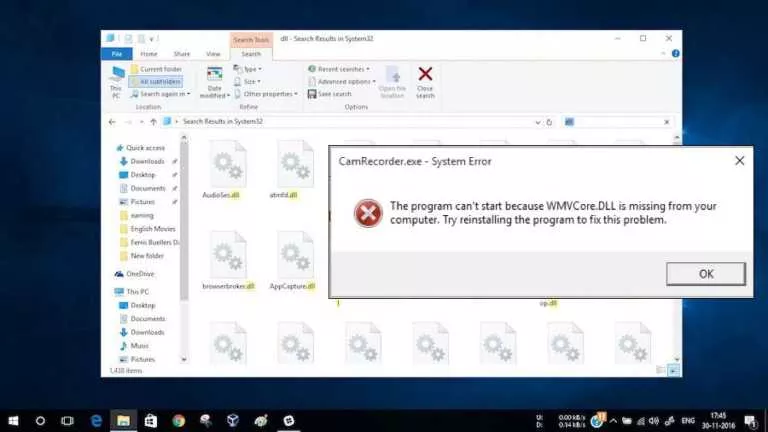
Short Bytes: After encountering a system error popup with the mention of a missing DLL file, ever…

Short Bytes: There are different chassis types available for computers like laptops, desktops, towers, workstations, etc. It’s…

Short Bytes: The 4G technology based on the LTE standard has reached most parts of the…

Short Bytes: C and R are one of the most popular single letter programming languages. There…
Short Bytes: Command Prompt or CMD is a command line interpreter in the Windows family of…
Short Bytes: Many of you might be using sudo and su in terminal every day to accomplish different…
Short Bytes: The first thing that comes to our mind for the term programming language is…

Short Bytes: Hackintosh is the nickname given to the non-Apple computers running Apple’s OS X or…
Short Bytes: Sudo command is one of the most used tools by Linux system administrators. Windows…