PPP (Point to Point Protocol): Components And Characteristics You Should Know About
Often termed as “PPP,” point to point protocol is a data link layer protocol which is used to set up a direct connection between two networking nodes. Below are some of the characteristics of PPP:
Characteristics of Point to Point Protocol
- As mentioned in the beginning, PPP resides at the layer two of the OSI model.
- This protocol supports other essentials such as authentication, error detection, link quality monitoring, load balancing, compression, etc.
PPP basically redefines the format of the frame to be exchanged between two devices. Once the format is set, both of devices can exchange the packets easily.
Components of PPP
To make PPP a successful protocol, there are certain essential components which form the basic building blocks of this protocol.
- Encapsulation
- Link Control Protocol (LCP) and,
- Network Control Protocol (NCP)
1. Encapsulation in PPP
Point to point protocol encapsulates the network layer packets in its frames. The fact that PPP can encapsulate any network layer packet makes PPP layer three protocol independent and also capable of carrying multiple Layer three packets over a single link.
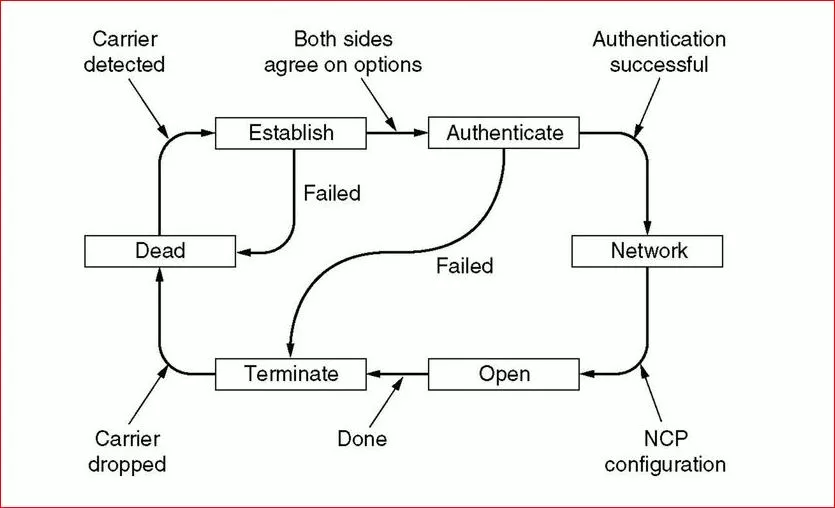
2. Link Control Protocol
Link Control Protocol is the second component of PPP. The main purpose of LCP is to build and maintain data-link connections. Below are some of the functionalities of this sub-protocol:
2.1 PPP Authentication
PPP uses its Authentication method to identify the remote device.
Scenario
Let’s say there are two routers R1 and R2. R1 has some data for R2 and wants to send the same to R2. But before sending the data, R1 just wants to make sure that the R2 is in Real “R2”. To authenticate its genuineness, R1 will initiate an authentication process in where R2 will have to prove its identity.
There are two authentication methods that PPP uses for authentication:
- PAP (Password Authentication Protocol)
- CHAP (Challenge Handshake Authentication Protocol)
2.1.1 PAP (Password Authentication Protocol)
PAP authentication is a two steps process. It goes like this:
Scenario: Router two wants to authenticate itself to router one.
- In step one, router two will authenticate itself to router one by sending its username and password in clear text.
- Upon receiving it, router one will check its database and match the credentials.
- Upon matching the credentials, router one will either accept or reject the router two request.
It should be noted that PAP authentication between two routers happens during the connection establishment only. Once the connection is already set up, no more sequential authentication is done for that particular session.
2.1.2 CHAP (Challenge Handshake Authentication Protocol)
Unlike PAP, CHAP is not only used for the initial connection set up but also, sequential authentication is performed to make sure that router is still communicating with the same host. If any sequential authentication is failed, the connection will be terminated immediately.
CHAP authentication is a three steps process. It goes like this (scenario remains the same as of PAP)
- In step one, R2 sends its username but without a password to R1.
- In the next step, R1 will check its database entry. This database contains a list of the hosts along with their credentials that are allowed to communicate with R1.
- If R2 is not found in the R1’s list, the connection is terminated then and there only.
- Otherwise, if R2 is found in the database list, then R1 will generate a random key. Using that random key and stored password, R1 will run the MD5 algorithm to create a hashed value.
- R1 will send this hashed value along with the random key to R2.
- R2, using the random key, will also run the MD5 algorithm on its password to generate a hashed value.
- Then it will compare both of the values. If both of the values match, R2 will send the acknowledgment.
The advantage of using CHAP over PAP in PPP (point to point protocol) is that the actual password is never sent across the link. So anybody tapping the wire will never be able to reverse the hash to know the original password.
2.2 Compression
Link Control Protocol (LCP) uses compression to increase overall data transmission speed while saving bandwidth at the same time. LCP compresses data at the sending end and decompresses the same at the receiving end.
2.3 Error Detection
LCP utilizes a tool called LQM (Link Quality Monitoring) to monitor different interfaces for their error percentage. There is a threshold value that has been defined for each interface. If a faulty interface exceeds the threshold value, LCP disables that interface.
2.4 Multilink
LCP can combine two physical links logically in such a way that they seem a single logical connection at layer three, i.e., the network layer. For example, if there are two connections of 128 Kbps then multilink will combine them in such a way that at layer three, they appear as one 256 Kbps connection.
You can also think of multilink as link aggregation technology. However, with the multilink the chances of receiving the packets out of order, because of the multiple links, become high.
2.5 Loop Detection
Point to point protocol is also famous for detecting the looped connections. To detect a loop, a node, while sending the PPP LCP messages, might also tag along with a magic number. If the line is looped, the node will get back its sent magic number in return. Otherwise, the node gets the peer’s magic number.
3. Network Control Protocol (NCP)
We already know that PPP works in data link layer of the OSI model. The data which comes from the upper layers such as Transport Layer or Network Layer has to be fully compatible with the PPP. For the same purpose, NCP was discovered.
Don’t forget to read our complete coverage on Computer Networks.