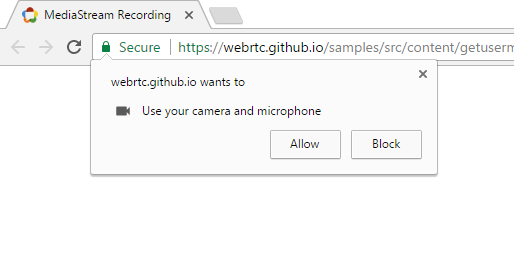
Google Downplays Chrome Bug That Allows Websites To Secretly Record Audio & Video
A Chrome bug was reported to Google by AOL web developer Ran Bar-Zik. He told Bleeping Computer that he had discovered it while checking a website running WebRTC code. WebRTC allows websites to record streams for live streaming to other devices across the internet.
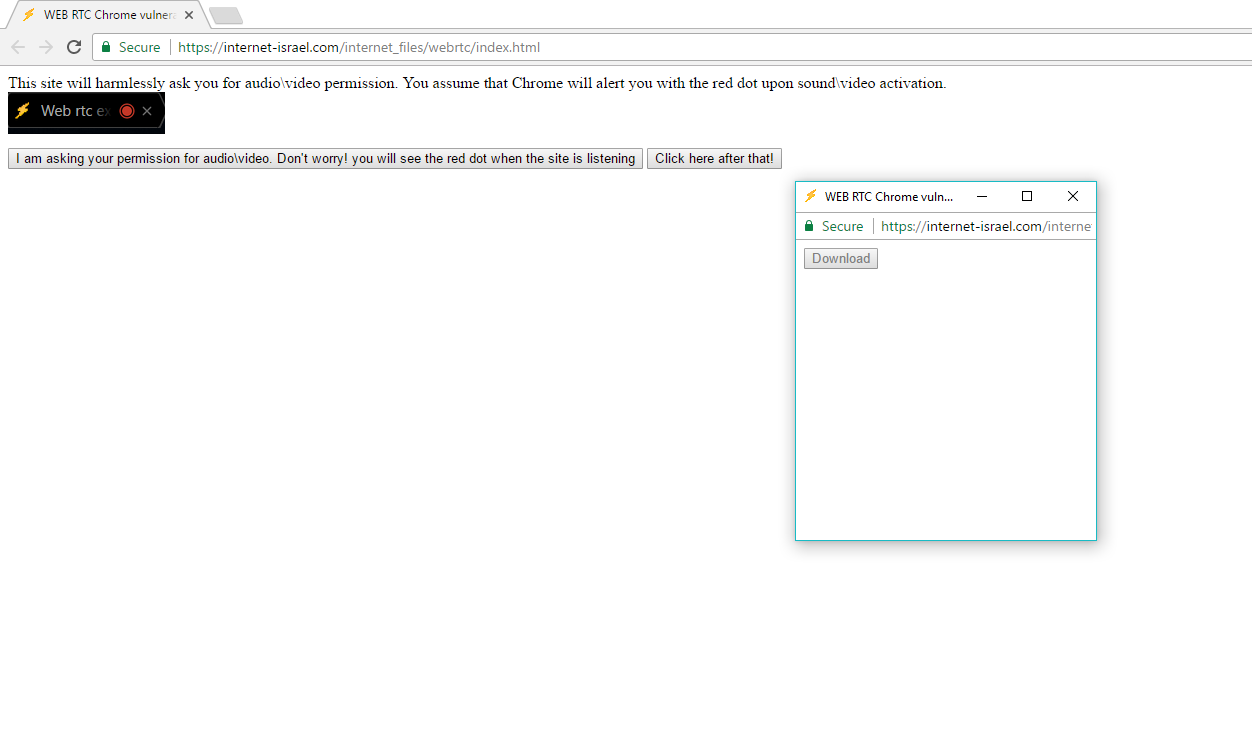
Due to the bug, websites can record audio and video content without showing the visual indicator. Still, the site requires user’s permission to access the microphone and webcam. So, the situation isn’t that serious. But it doesn’t mean it can’t be exploited.
Also Read: Hackers Behind NSA Data Leak Launch “$21,000 Zero-Day Dump” Subscription For Whitehats, Govts.
According to Ran, the access permissions are given for a whole domain, so, it’s possible not to use the same tab to record streams. The attacker can show a pop-up (headless Chrome window) running the code to record audio and video streams. This pop-up won’t carry the red dot. To verify his claims, he created a test popup himself.
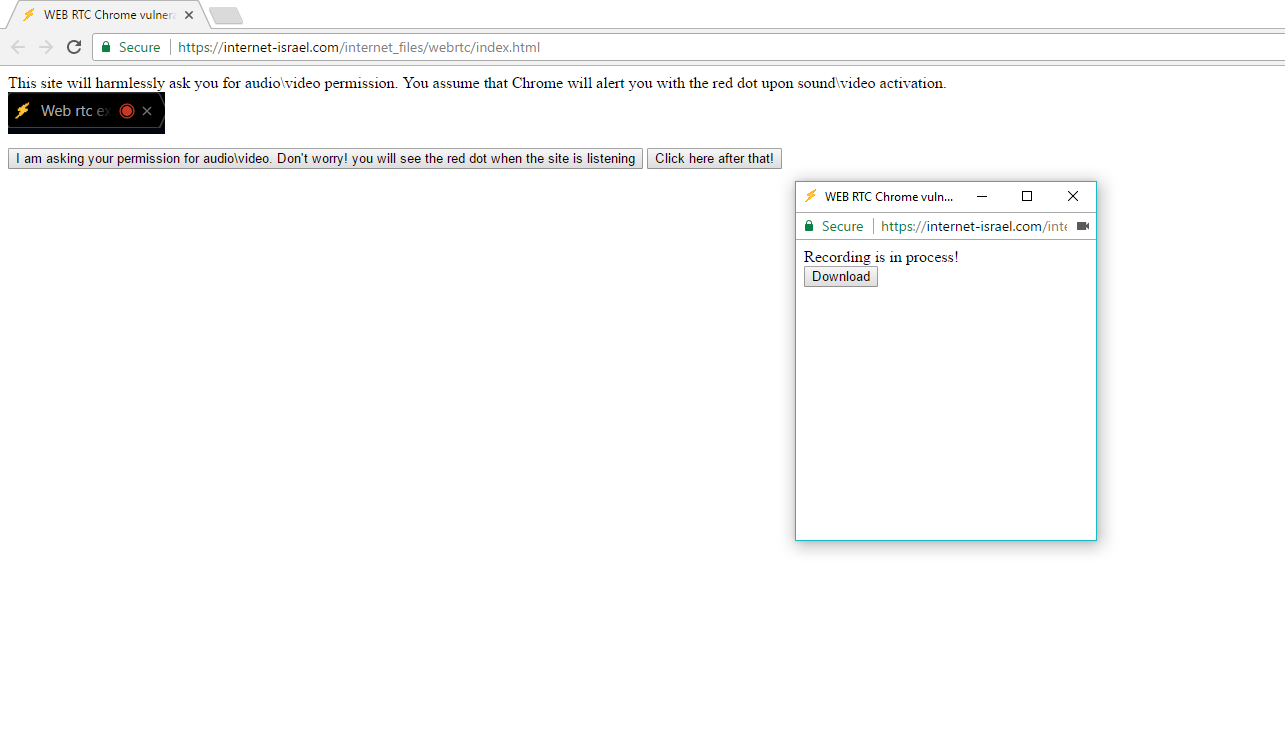
The demo pop-up is included in the bug report Ran submitted to Google. After gaining permission, the pop-up records 20-second audio clips and provides a download link for the same. The code for his proof-of-concept is available as a zip file.
Contrary to what Ran believes, Google doesn’t consider the bug as a threat at all. That’s because the visual indicator isn’t present on all platforms where Chrome is available.
“This isn’t really a security vulnerability – for example, WebRTC on a mobile device shows no indicator at all in the browser. The dot is a best-first effort that only works on desktop when we have chrome UI space available. That being said, we are looking at ways to improve this situation,” Google replied.
It might be possible that some people unknowingly grant access permissions and fail to recognize anything fishy due to the inconsistencies in the UI. This can lead to more sophisticated attacks.”Real attacks will not be very obvious,” said Ran when comparing these situations to the demo pop-up.
An evil pop-up might not even ask for a click like Ran’s demo. It can be as simple as an annoying advertisement which most of us don’t even realize is present alongside other browser windows until we close the web browser.
It’s possible for an attacker to time the pop-up according to their needs. It could possibly appear just for a moment to take a picture of the user or maybe even for hours.
Instead of setting up a whole website, according to Ran, it’s possible for an attacker to exploit cross-site scripting (XSS) flaws on trustworthy websites which have acquired access permissions from the user. The attacker can leverage the XSS flaws to deliver the attack code.
Google might not be entirely wrong
It’s unlikely that Google will push a bug fix as they don’t find Ran’s finding that alarming. Given the absence of the visual indicator on different Chrome variants, they might not be entirely wrong on their part. Also, the user plays a major role and has a choice of denying when asked for permissions.
Got something to add, drop your thoughts and feedback.
Also Read: Google Is Testing “Chrome Home” For Android, What The Experiment Actually Is?