Hacker Cracks Windows Account In Less Than 1 Min, Doesn’t Know If It’s A Bug Or Feature
Short Bytes: It is possible to gain access to any logged-in user account on any version of the Windows OS. The attack has been demonstrated by an Israel-based researcher. It is possible to hijack an active session after privilege escalation on a Windows machine. And the process takes less than one minute. However, it’s unclear if it’s possible due to a bug or a feature.
Alexander Korznikov, a security researcher based in Israel, has described a way to gain access to any local user account on a Windows machine without having any idea about the login credentials. It has been confirmed by another security researcher Kevin Beaumont that the attack works for all Windows versions.According to Korznikov, the attack requires physical access to the target machine, but it can also work over a remote desktop session on a hacked machine. However, for the attack to work the target user must be logged in on the computer.
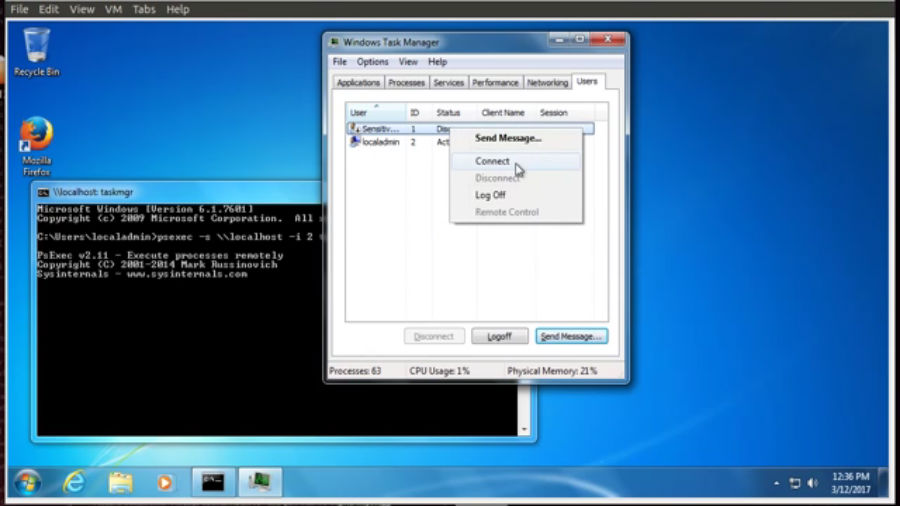
The attacker can use built-in Windows CMD commands to harness elevated privileges on the machine. Using the NT AUTHORITY/SYSTEM — a local account with highest privileges — he will be able to hijack another active user session without the need of any login credentials. All of the work takes less than one minute of time.
Korznikov says he is not the first one to perform this kind of privilege escalation and session hijacking. Also, he isn’t sure if he was successfully able to perform the attack because of a feature or a zero-day vulnerability. A similar hack was performed by a security researcher Benjamin Delpy (link in French) in 2011. This flaw is known to Microsoft since last 6 years and the company assumes that this is how Windows is supposed to work.
It might be a bug which Microsoft was too lazy to fix. But Delphy told Korznikov that it’s the actual design flow of the Windows API where the admin has the freedom to do anything.
“If some unprivileged user becomes admin using some kind of local privilege escalation – that’s the problem and not the design flow we are talking about,” Delphy said.
“You can do everything, even patch terminal services the way that it will accept your token and allow shadowing mode, without user’s knowledge.”
The videos presented below are a proof-of-concept of Korznikov’s session hijacking attack.
Windows 7 via Task Manager:
https://youtu.be/oPk5off3yUg
Windows 7 via command line:
https://youtu.be/VytjV2kPwSg
Windows 2012 R2 via service creation:
https://youtu.be/OgsoIoWmhWw
You can read Korznikov’s blog post to know more the about the attack.
If you have something to add, drop your thoughts. And don’t forget to tell us your feedback.
Also Read: 12 Best Operating Systems For Ethical Hacking And Penetration Testing | 2017 Edition