PS5: Release Date, Design, Price, Specs, All Confirmed Games For PlayStation 5
The upcoming PS5 release date was leaked a few days ago via secret internal e-mail. According…

The upcoming PS5 release date was leaked a few days ago via secret internal e-mail. According…

With the amount of data increasing on a daily basis, storage techniques have not evolved as…

After a technical snag that delayed the launch of Chandrayaan-2; ISRO finally launched the spacecraft last…

Managing your IT infrastructure can be incredibly difficult. This is why we have centrally managed systems…

CPU comparison between Intel and ARM has been a topic since 2010 when Steve Jobs predicted…

Earlier this year, Samsung released its flagship lineup including the Galaxy S10, S10+, and S10e. These…

Xiaomi has once again challenged its rivals in the budget segment by launching Redmi Note 7…

Over the years, Peel Remote app has deteriorated from one of the top universal remote apps…

Android has probably more updates than Indian spices in Sundar Pichai’s house. From Android 1.5 Cupcake…
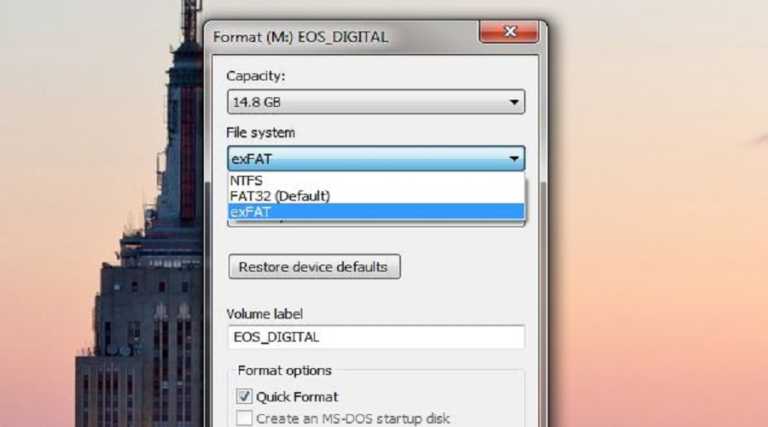
FAT32, NTFS, and exFAT are the three file systems we commonly use for Windows and storage…