What Is IP Spoofing And Denial Of Service (DOS) Attack?
Short Bytes: IP Spoofing and Denial of Service are the two most famous attacks that an…

Short Bytes: IP Spoofing and Denial of Service are the two most famous attacks that an…

Short Bytes: When a wireless network is deployed, authentication is the first thing that needs to…
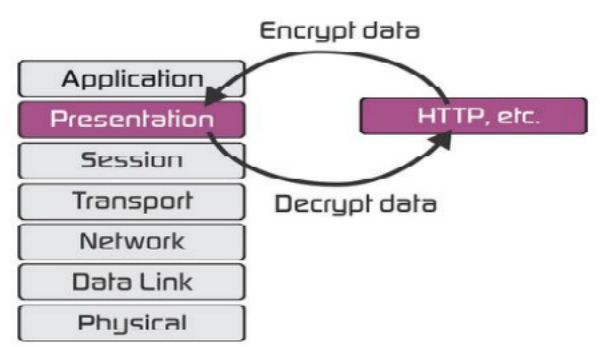
Short Bytes: Presentation layer comes next after the session layer in the OSI model of layers in…
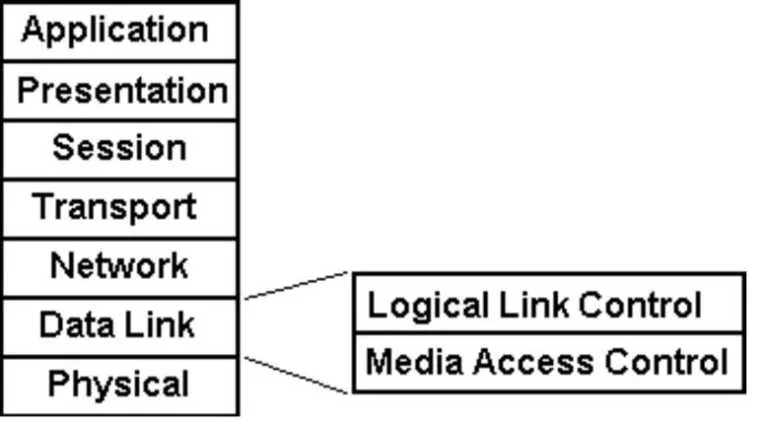
Short Bytes: If the MAC layer is responsible for the medium access then LLC layer is responsible…
Short Bytes: Why the physical layer is so important in the OSI model? What roles are…
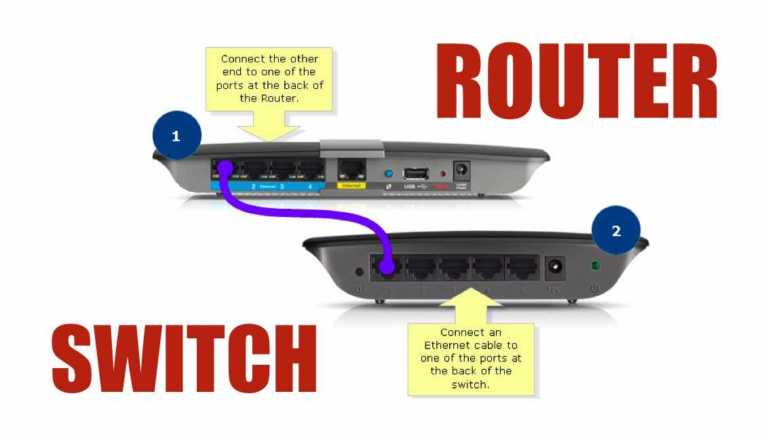
Short Bytes: Switch vs router – which one works where? Which one should be used for faster…

Short Bytes: Hub vs Switch – which one is better? Which one should be used for faster…
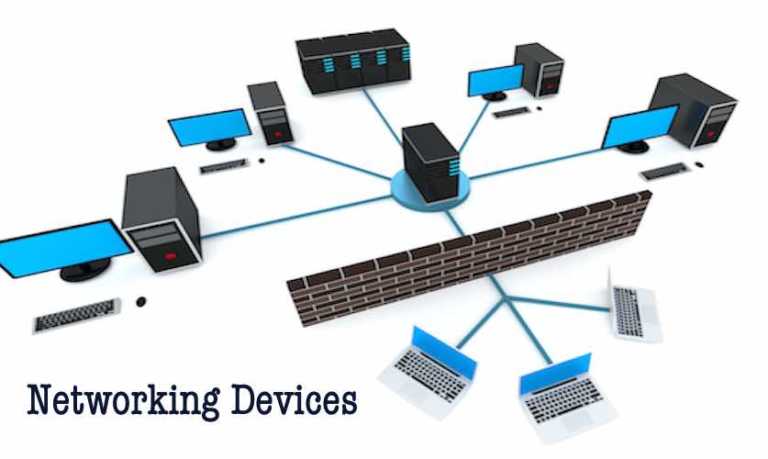
Short Bytes: Different networking devices have different roles to play in a computer network. These network…
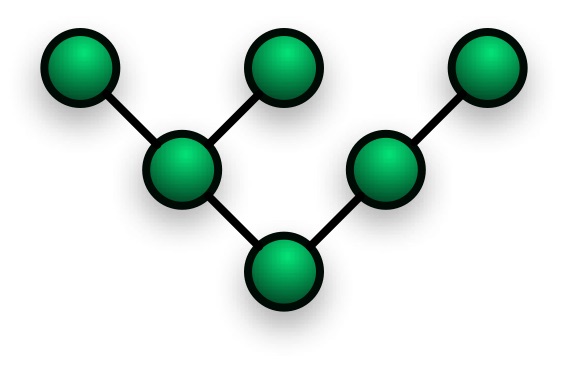
Short Bytes: Tree Topology derives its roots from bus and star topology. Even though a tree topology is…
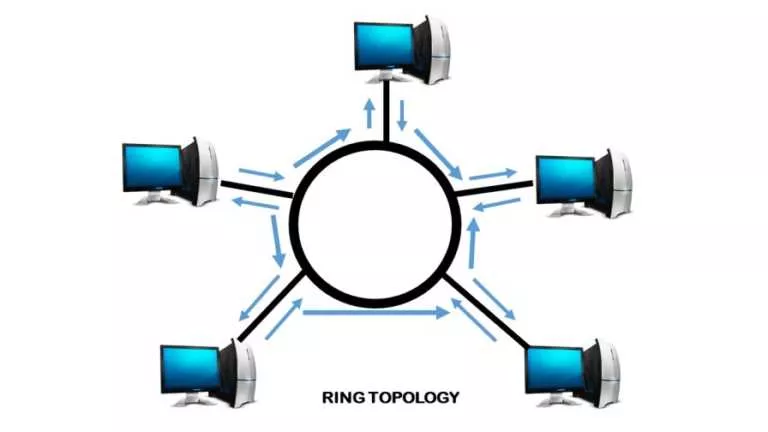
Short Bytes: Do you know about Ring topology or a Ring network? Here, I’ll tell you the…